Your Email Has Been Hacked… Just Yawn??
Another friend’s Yahoo email account was broken into this morning.
Link in the Email
My clue was that he sent me an email at 4:11 am. And, the only content of the message was a link to a page on the Internet that runs a PHP programming script.
The message was sent to me, his sister, his ex across the continent, and bunch of other people I don’t know. The email had a long TO: list that looked like a random group of emails from my friend’s address book.
So, another person’s email account was compromised. Probably hackers went through and guessed his password. Or, maybe his email address and password were stolen from another site that had been broken into. Do we, or he, care?
The recipients of the email shouldn’t worry, as long as they don’t click on the link and visit the site in Latvia (.lv). I am sure that waiting on the .php destination page there is a malicious script that will try to infect the computer of any visitor that goes there. Even so, you’d probably have to also click on a confirmation box to run a program before you got into trouble. If you receive an email like this, you’re okay so long as you delete it without clicking on any link.
My friend, however, has a few worries:
- First, he needs to stop the damage. He should go to Yahoo and try to regain control of his account. If they bad guys are nice, they didn’t change the password. He can log into Yahoo and pick a different, stronger password. Some bad guys are not so nice. They will change the email password so that you’re locked out of your own email account. In that case, you’ll need to contact Yahoo (or whoever owns the hacked site) and ask them to help.
- The bad guys controlled/control his email account for a while. If they are truly evil, their programs visited all of the major banks, credit card companies, online stores, investment houses, etc. They typed in my friend’s email address, saying that they had lost their password. Many stores and financial institutions responded with an email link to reset the password. The bad guys, who had access to the Yahoo email account, clicked on the reset password link, created a new password, and gained control of my friend’s financial resources.My friend should go to every place he used the Yahoo address and enter a different email address for the account. He should also look over recent transactions to make sure his account hadn’t been compromised.
- The bad guys could go to every online store, and see if the combination of the email address and Yahoo password logged them in. If my friend reused that password anywhere where he also used the Yahoo email address, that account is vulnerable. My friend should change the password everywhere he used the same credentials he used for his Yahoo email account.
He should also look over recent transactions to make sure his account hadn’t been misused.
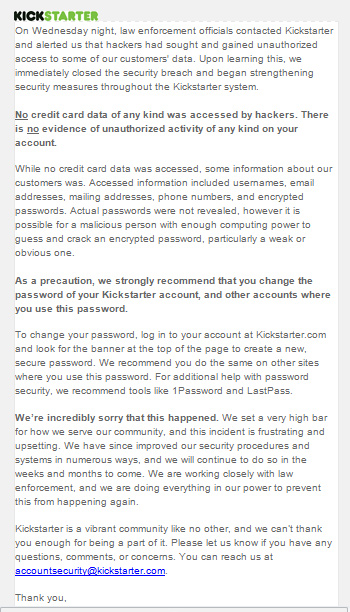
You should use unique passwords for every site, especially sites like banking or ordering sites which remember your credit card number. When you use unique passwords, if a site is broken into you have to change your password for that one site. If you share passwords among sites, you have to change that password on every site it’s used when it’s compromised on any of the sites. — from a post about Kickstarter being hacked
My earlier post recommends that you sign up for the free password management program, LastPass. I am going to suggest, really suggest strongly, that my friend do that today!

 More and more sites are using
More and more sites are using 