So, How Does Malware Get on Your Computer?
No one intentionally installs an application that is going to encrypt their files until they pay a ransom, log their keystrokes and report their bank passwords to crooks in Russia, or hijack their web browser to show ads instead of the sites they want to go to. Bad guys have to trick you into going to some web site, looking at an infected message, or clicking on a link to allow them to download their toxic programs.
Basically, YOU have to give the jerks permission to infect your computer.
You’re not likely to click on a button that says, “YES, Download your malware and steal my identity!” 
So the people who want to get inside your computer send you clever, urgent messages to get you to unleash their poisonous computer code on your computer. Frankly, the inventiveness and smart marketing techniques these folks use are praiseworthy.
Here’s the invitation to be a sucker that arrived in my email yesterday:
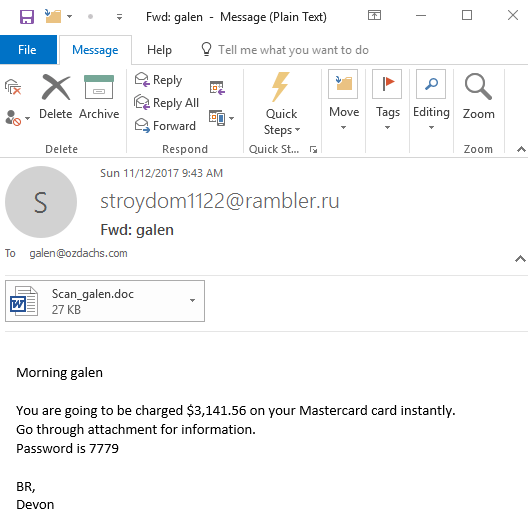
Look! My Mastercard is going to charged instantly! (A classic injection of urgency to get someone to act NOW!)
I can see the details of this instant charge — and also unleash the evil software embedded in the Word document — by simply clicking. I mean, who wouldn’t want to know why their Mastercard is about to be charged a hunk of money?
Well, probably someone like me who doesn’t have a Mastercard. But, more importantly, YOU! Even if you have a Mastercard, you should be in the habit of NOT clicking to open attachments or follow links on emails you’re not expecting.
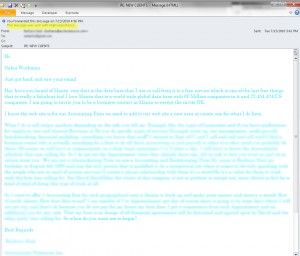
In this case, the scammers messed up somewhat by showing a return address of stroydom [email protected]. That’s an email address without a name, and the “.ru” means it supposedly comes from is from RUssia. If they’d been smarter, they would have used a generic From name and spoofed the return address, something like “Sarah Jones <[email protected]>”. Even better would have been spoofing the name and email address of someone I know, if that had access to my email address book.
Every day I get messages trying to trick me into clicking a box or a link that would instruct my computer to let the would-be hackers install their evil code on my system. Then they could take over my machine and lock up my data for ransom… or do something more subtle like watch me login to my bank’s website so that they can learn my password. Many of these attempts are stopped by my email’s spam/malware filter, but some get through.
Here’s what the latest attempt to hoodwink me reminded me:
- Don’t click on anything in an email unless you know the person who sent the email AND you were expecting a message from them.
- Use Chrome or other browsers who warn you if you try to go to a site on their dirty list.
- Use up-to-date antivirus software. That will block the downloading and installation of evil programs… so long as the antivirus program knows about it.
Follow these guidelines and don’t get shocked into clicking where you should’t!
A $3,100 unexpected charge on your Mastercard? Don’t panic. And, don’t click!